articles
Build your own VPN node with Traefik v2, MTProto Proxy, WireGuard and BIRD 2.0 / Part 1
- Publish Date
- Solution Architecture
- Server Side Platform Overview
- CPE Side Platform Overview
- References
Today plenty of people already know what VPN 1 is and why they need to use it. So many governments have joined Internet censorship, new examples appear every year all over the world. In this article we build uncommon installation for you own private VPN node.
Publish Date
- 2021-04-19
Solution Architecture
Our router is represented by Traefik v2 2 reverse proxy, it hides SNI 3 routed MTProto 4 proxy in Fake TLS 5 mode and WireGuard 6 with BIRD 2.0 7.
Note: We will not attempt to build SD-WAN 8 through this series of articles, nor will we implement any software controller for management plane. These articles describe topology contained only one VPN host communicating with two Linux-based CPEs 9. But this doesn’t mean it cannot be scaled horizontally.
As we intend to make our VPN node stable and reachable as much as possible, we decided to use TCP and UDP ports to mimic to existing everyday applications:
- TCP/443 for MTProto
- UDP/443 for WireGuard
But please bear in mind, the WireGuard does not focus on obfuscation 10 and does not try to hide itself from firewalls with DPI 11 engine. We also will not try to hide WireGuard from ISP’s backbone, but just select UDP/443 port that is used by QUIC 12 protocol and is usually not blocked or inspected due to complex implementation for such a huge amount of traffic.
Overall diagram:
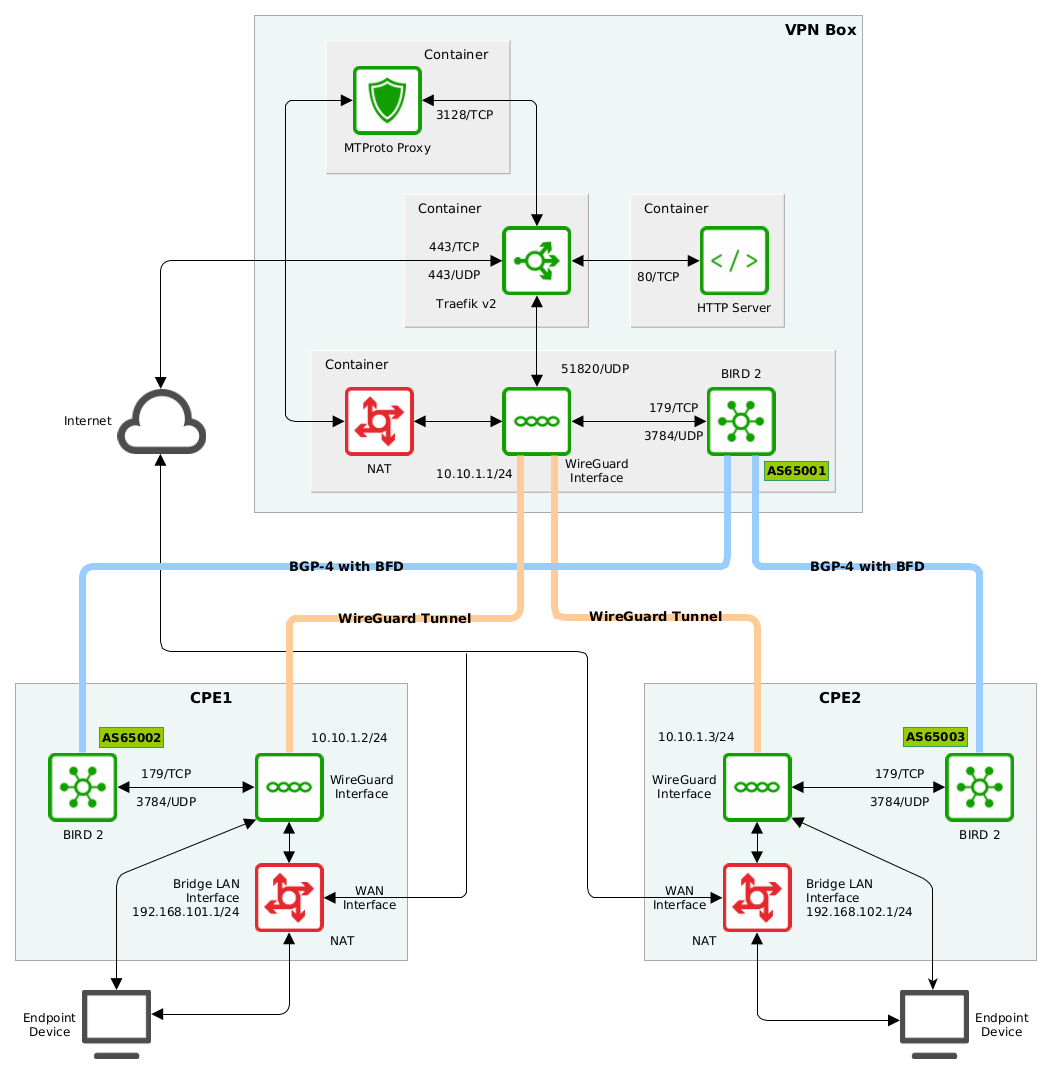
Server Side Platform Overview
The server side platform doesn’t matter as we use containerization. For this article use Ubuntu Server 20.04 LTS 13 as platform and Docker 14 with Docker Compose 15 for simple containers orchestration. Let me describe components one by one.
Docker and Docker Compose
Docker has been installed from standard system repositories along with Docker Compose. The installation will contain four services: BIRD 2.0, WireGuard and NAT will be packed into single container with supervisord 16 to run multiple services, Traefik v2, MTProto Proxy and Simple HTTP service will run as independent containers. Docker Compose helps us to orchestrate microservices topology, Compose 2.4 specification will be used as there we still able to create networks with names and gateways 17.
Of course, we would love to use Podman 18 instead of Docker, however, at the time of writing, the Traefik v2 is still not fully compatible 19 with Podman.
Traefik v2
Traefik v2 is an open source edge router that provides publishing of services, it receives requests and finds out which components are responsible for handling them. This article is not intended to introduce you to Traefik v2 configuration, please check the official documentation.
WireGuard
WireGuard is a free and open source software application and communication protocol that implements VPN techniques to create secure peer-to-peer connections in routed or bridged configurations. In charge of tunneling private traffic.
BIRD 2.0
BIRD 2.0 is an open source implementation for routing Internet Protocol packets on Unix-like operating systems. It will be responsible for BGP 20 and BFD 21 communications. It’ll push selected network prefixes toward client side while BFD is used to quickly shutdown BGP session when remote client stops responding to BFD probes.
MTProto Proxy
MTProto proxy was created to bypass many kinds of government firewalls that block access to Telegram. The Fake TLS mode is a method that makes proxy traffic look like normal TLS. Therefore, it is more difficult to detect such a proxy, and therefore block Telegram too. Protects our connection to Telegram servers making remote breakout.
HTTP Server
A simple HTTP server for holding any additional files which makes our installation look like HTTPS server.
CPE Side Platform Overview
CPE platform may vary across *nix family, OpenWrt 19.07 22 was chosen for this article with additional packages installed:
- bird2, bird2c, bird2cl
- wireguard, wireguard-tools, luci-app-wireguard, luci-proto-wireguard, kmod-wireguard
- json4lua, luasec
- ca-certificates, openssh-server, openssh-client, openssh-keygen, shadow-common, shadow-useradd, shadow-userdel, unzip, zip, tcpdump, ddns-scripts, ddns-scripts-services, sudo
BIRD 2.0 works in pair with WireGuard client to create automated routing scheme in the following sequence:
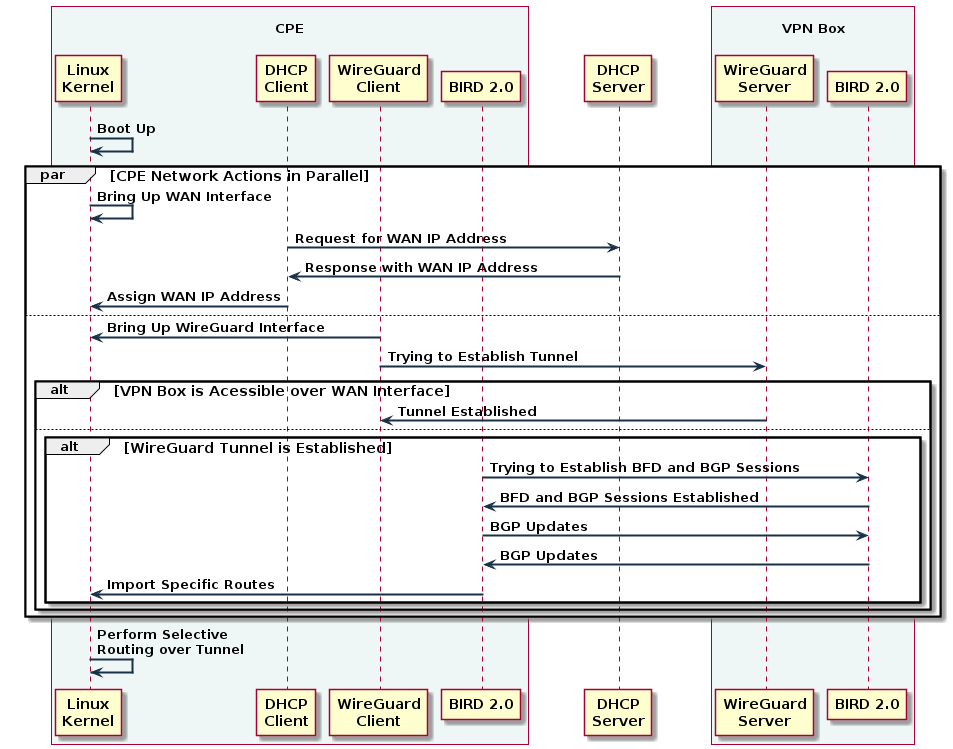
Part 2 explains server side configuration.
References
1. Virtual Private Network ↩
2. Traefik v2 ↩
3. Server Name Indication ↩
4. MTProto Mobile Protocol ↩
5. MTProto Fake TLS ↩
6. WireGuard: fast, modern, secure VPN tunnel ↩
7. BIRD Internet Routing Daemon 2.0 ↩
8. SD-WAN ↩
9. Customer Premises Equipment ↩
10. WireGuard does not focus on obfuscation ↩
11. Deep Packet Inspection ↩
12. QUIC transport layer network protocol ↩
13. Ubuntu Server 20.04 LTS ↩
14. Docker ↩
15. Docker Compose ↩
16. Supervisor: a process control system ↩
17. Docker Compose: support IPAM gateway in version 3.x ↩
18. Podman ↩
19. Traefik: Podman support ↩
20. Border Gateway Protocol ↩
21. Bidirectional Forwarding Detection ↩
22. OpenWrt ↩